Yesterday someone stole my daughter’s new smartphone from a school locker. On Friday, a good friend’s iPhone 3GS disappeared from a car dealership, while he was talking on it. Both stories, which go oddly together, are cautionary tales about social media, cloud computing and the risks of identities stolen with the hardware.
Stolen phones used to conjure fears of minutes usage overages or big bills from calls placed to faraway places. Now the cost could be you.
The story of my good friend Andy begins on a sunny Southern California afternoon. Andy is a small business guy who runs bookstores and Halloween costume shops in the Los Angeles and San Diego areas. He’s a boisterous, happy fellow who walks around with a bluetooth earpiece that might as well be surgically attached to his head. Andy’s a talker. Constantly. If it’s not someone present, it’s to someone on the phone.
Andy got his first iPhone in summer 2008, at my recommendation. He upgraded to iPhone 3GS a few months ago. For Andy, iPhone is more than just talk. He uses it for email, texting and running applications that support his business, including built-in photo and video capabilities and others downloaded from Apple’s App Store. “My iPhone is my life,” I’ve heard him say.
Perhaps he is too free with his life. Andy received a phone call while sitting in the car dealer showroom. He had an appointment elsewhere and got up to leave. All the while, Andy chattered away into the Bluetooth headset. It was only after he got in his SUV that Andy realized, “Oh my gosh, I left my iPhone inside!” So, still talking to someone via Bluetooth, Andy mosied back to the dealership for his iPhone. It was gone.
Andy interrupted the caller to ask if anyone had seen his iPhone. Surely it was nearby, because he still had a connection to the caller. No one seemed to know where the phone could be. Andy again felt reassured because he still had an active connection, so the phone had to be close by. Somewhere. Andy’s good nature worked against him. Yes, the phone probably was nearby—in somebody’s desk drawer, pocket, briefcase or purse. I would have disconnected the caller, picked up a land line and called the phone to hear it ring. But Andy didn’t think to do this right away. Later, when it was too late to make that important call, he realized that someone stole the phone.
CLIQ is Snipped
My daughter’s story is different, but worth switching to now so as to tie together lessons from both tales later. On November 2nd, launch day, my daughter got a brand, new Motorola CLIQ from T-Mobile. A few weeks earlier I moved the whole family from AT&T to T-Mobile. That’s right, no more iPhones for us. The number of dropped calls and failed connections had finally led me to abandon AT&T, after six years a customer. I’ll blog switch experience later, but for now will say T-Mobile hasn’t dropped one call yet.
The switch meant buying new phones, because our Nokia handsets used AT&T 3G frequencies. I sold three Nokias: two N95s and N97 to pay for new phones. My daughter asked that I hold onto the Nokia E71.
The CLIQ features a social media interface that Motorola calls MOTOBLUR, which keeps a pretty much persistent connection to services like Facebook, MySpace and Twitter. MOTOBLUR updates status messages, user photos and other information. While my daughter fancied MOTOBLUR, CLIQ’s keyboard mattered more for her in the first few days using the smartphone.
She had taken the E71 or CLIQ to the local high school for more than two months without problems. Perhaps that’s why she let down her guard and put her belongings into an unlocked locker during physical education class yesterday. When my daughter checked the phone after class, but it was gone from the case. At first, “I thought it was loose in my bag,” she said. Sometimes when rushed between classes, my daughter tosses the phone in her tote bag, rather than put it in the case.
The phone was gone. Stolen. But nothing else. Either the thief was novice and afraid or experienced and crafty. By leaving the phone case—and lunch money—the thief increased the likelihood the CLIQ wouldn’t be noticed missing until after school hours. But my daughter most certainly noticed and called me on a school phone around Noon PT.
Find and Wipe
Here’s where the two stories intersect. Both smartphones contained personal information, including IDs and active passwords for accessing various online accounts. Neither my friend nor my daughter realized the risk. But I sure did. Both phones come with location and remote data wiping services, which could greatly diminish the risk. But there were complications.
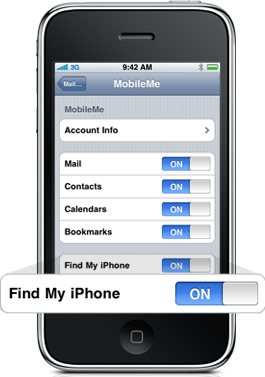 The iPhone data wiping and location service (“Find My iPhone“) requires a MobileMe account, which costs an extra $99 a year. Andy hadn’t signed up for MobileMe. I believe, but I am not certain, that Find My iPhone is enabled via Web service. If so, Andy could have signed up for MobileMe and activated the feature anyway, since the stolen iPhone synced to the cloud via push services. By the time he and I spoke about the theft, he had already purchased a new iPhone 3GS and activated a new AT&T SIM card. Not until we talked did Andy understand that he should change all account passwords.
The iPhone data wiping and location service (“Find My iPhone“) requires a MobileMe account, which costs an extra $99 a year. Andy hadn’t signed up for MobileMe. I believe, but I am not certain, that Find My iPhone is enabled via Web service. If so, Andy could have signed up for MobileMe and activated the feature anyway, since the stolen iPhone synced to the cloud via push services. By the time he and I spoke about the theft, he had already purchased a new iPhone 3GS and activated a new AT&T SIM card. Not until we talked did Andy understand that he should change all account passwords.
My daughter’s data situation is more complicated. CLIQ comes with GPS location and data wipe services for free. But I needed access to my daughter’s MOTOBLUR account, which was created during initial phone setup. MOTOBLUR can be managed from a Web browser. Problem: I didn’t have her username or password. So I called the school and pulled her out of class for the information. But information was deficient. MOTOBLUR login failed, and there was no record of the email address she gave me for the account. So I called T-Mobile, which temporarily disabled the SIM card.
Hours later I called back T-Mobile customer service, which connected me to Android support. The tech support rep was extremely helpful. He eventually located my daughter’s account. Turns out she made a mistake during account setup and created a non-existent email address. Using an admin password, he accessed the MOTOBLUR account and also reactivated the SIM card. I wanted to locate the stolen phone.
But that turned out to be impossible. During initial CLIQ setup two weeks ago, my daughter was asked to activate GPS services. I said no because we both had concerns about battery life. As such, with GPS services disabled, the phone couldn’t be located. But the CLIQ could be remote wiped, which is what the Android tech did before disabling the SIM once more. Later, I obtained a new SIM from my local T-Mobile store.
But the story doesn’t end there. Android phones like the CLIQ are designed to solely sync to the cloud, even though photos and pics can be pulled from the device when connected to a PC. By comparison, iPhone can sync to both cloud and desktop. Andy easily synced the new iPhone 3GS to his PC, restoring photos, videos and other data.
When my daughter gets a new CLIQ (the phone was insured but with deductible), she will be able to sync accounts and contacts from the cloud. However, she has lost photos and videos taken on Friday for an English class homework assignment. Near as I can tell from MOTOBLUR information site, only contacts, social network accounts, messages and email are backed up to the cloud. Well, this might be the best “the dog ate my homework” story my daughter’s English teacher will ever hear.
Smarter Than the Smartphone
It’s commendable that Apple and Motorola/T-Mobile offer mechanisms by which consumers can find or wipe their smartphones. These kinds of capabilities shouldn’t be just for businesses. But should consumers have to pay Apple $99 to get such features? I don’t think so. Location finding and data wiping services should be standard for all smartphones. There is simply too much risk to individuals’ identities.
According to Gartner, manufacturers sold 41 million smartphones during third quarter, for a 12.8 percent year-over-year increase. Smartphones accounted for about 13 percent of worldwide handset sales. Nokia (39.3 percent), Research in Motion (20.8 percent) and Apple (17.1 percent) are the smartphone marketshare leaders.
During fourth quarter, smartphone sales could dramatically surge, given the number of new and interesting models, including the Motorola DROID and HTC DROID ERIS, among others. More people will be buying these smarter phones , but their user attitudes will carry forward from dumber handsets. Many new smartphone users won’t understand the data risks coming with convenience.
The risk and convenience intertwine with the cloud, where services are consumed and personal data and account information sync. In the case of CLIQ, MOTOBLUR consolidates access to multiple social networking accounts. The benefit carries great risk in the event the device is lost or stolen. Motorola’s failsafe mechanisms greatly mitigate the risk.
HTC uses “You” as part of its smartphone marketing campaign. It aptly describes exactly what’s going on with these device. You are the phone. Your life is in your backpack, briefcase, pocket or purse. If you lose the phone, do you lose your life? The answer may depend on whether you or someone else has access to your accounts and data.
Do you have a mobile phone story that you’d like told? Please email Joe Wilcox: joewilcox at gmail dot com.
